Today I'm trying to setup a test environment for an architecture we thought could solve some project problems.
The architecture is the following:
The installation is easy, just deploy the opensso.war inside the tomcat/webapps folder, giving Tomcat one gigabyte of memory (add JAVA_OPTS=-Xmx1024m in catalina.sh) and a fully qualified domain name to the host running tomcat (sso.smartlab.net alias for 127.0.0.1 in /etc/hosts). On first access to the http://sso.smartlab.net/opensso url (it's very important you use the fully qualified domain name on your first access as it's used for configuration) I simply ran the Default Configuration (suggested for test environments only) which requires just two passwords: the amAdmin credentials will be used to access the administration console while the amAgent credentials will be used .
After I installed the OpenSSO policy agent on top of JBoss 4.2. First of all you need to create the J2EE policy agent profile in OpenSSO. To perform this you have to access the OpenSSO administration console (username amAdmin, password the one you specified during initial configuration) and follow the official instructions replacing the informations providen there with your test environment infos; mine were:
I'm just performing an initial test of the architecture so I'm cloning the server/default folder of my JBoss 4.2 installation to server/sso, cleaning it up from previous work and editing the deploy/jboss-web.deployer/server.xml to switch the connector ports to 8180 (HTTP) and 8109 (AJP).
I unzipped the JBoss Policy Agent 3.0 package (unpacked in /opt/jboss/opensso removing the messing directory structure j2ee_agents/jboss_v42_agent) then I created a file with the agent password
$> echo "agent password" > /opt/jboss/opensso/agent.pwd
then I ran the bin/agentadmin script using this informations:
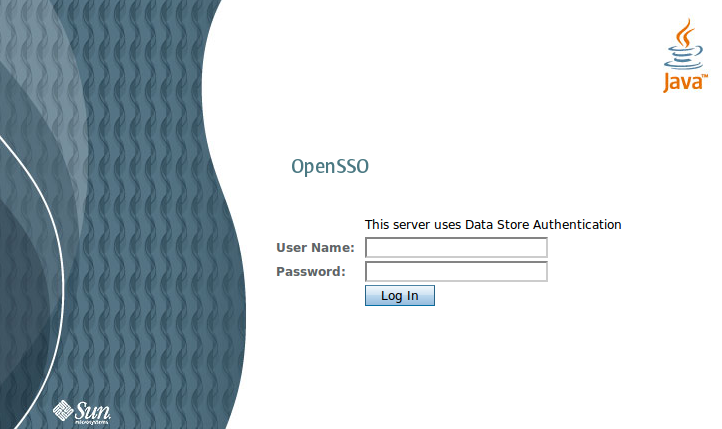 I then ran my JBoss test instance with /opt/jboss/bin/run.sh -c sso and everything seems working: I tested it trying to access the http://test.smartlab.net:8180/opensso-agent application being redirected to the OpenSSO login page on http://sso.smartlab.net/opensso.
I then ran my JBoss test instance with /opt/jboss/bin/run.sh -c sso and everything seems working: I tested it trying to access the http://test.smartlab.net:8180/opensso-agent application being redirected to the OpenSSO login page on http://sso.smartlab.net/opensso.
The last test was about securing the JBoss JMX Console through OpenSSO. The activity required me to:
Ok, then let's try to log into the JBoss JMX Console, but with which credentials?!? On my first try I used the OpenSSO Administration Console superuser credentials (amAdmin/adminadmin) but I encountered a redirection loop failure thus discovering my setup wasn't ready yet. Googling a little bit I discovered this error can be simply solved adding an addition parameter for the JVM to the Tomcat configuration: JAVA_OPTS="$JAVA_OPTS -Dcom.iplanet.am.cookie.c66Encode=true".
Solved the problem and going back to the JMX Console I got a 403 (resource forbidden) error and after some investigations I discovered the easiest solution was to tell OpenSSO to simply apply a limited policy of type SSO_ONLY (Access Control > Top Level Realm > Agents > J2EE > JBoss > General add a jmx-console=SSO_ONLY map entry).
In the near future I wish to try the usage of the OpenID 2 standard on OpenSSO, I've found some instructions on another blog but I hadn't the time to investigate yet.

The architecture is the following:
- JBoss 4.2 or 5.1 (the choice is delayed)
- OpenSSO 8
- WSO2 ESB
- Liferay 5.2
The installation is easy, just deploy the opensso.war inside the tomcat/webapps folder, giving Tomcat one gigabyte of memory (add JAVA_OPTS=-Xmx1024m in catalina.sh) and a fully qualified domain name to the host running tomcat (sso.smartlab.net alias for 127.0.0.1 in /etc/hosts). On first access to the http://sso.smartlab.net/opensso url (it's very important you use the fully qualified domain name on your first access as it's used for configuration) I simply ran the Default Configuration (suggested for test environments only) which requires just two passwords: the amAdmin credentials will be used to access the administration console while the amAgent credentials will be used .
After I installed the OpenSSO policy agent on top of JBoss 4.2. First of all you need to create the J2EE policy agent profile in OpenSSO. To perform this you have to access the OpenSSO administration console (username amAdmin, password the one you specified during initial configuration) and follow the official instructions replacing the informations providen there with your test environment infos; mine were:
- Name : JBoss
- Server URL : http://sso.smartlab.net:8080/opensso
- Agent URL : http://test.smartlab.net:8180/opensso-agent
I'm just performing an initial test of the architecture so I'm cloning the server/default folder of my JBoss 4.2 installation to server/sso, cleaning it up from previous work and editing the deploy/jboss-web.deployer/server.xml to switch the connector ports to 8180 (HTTP) and 8109 (AJP).
I unzipped the JBoss Policy Agent 3.0 package (unpacked in /opt/jboss/opensso removing the messing directory structure j2ee_agents/jboss_v42_agent) then I created a file with the agent password
$> echo "agent password" > /opt/jboss/opensso/agent.pwd
then I ran the bin/agentadmin script using this informations:
- JBoss Server Config Directory : /opt/jboss/server/sso/conf
- JBoss Server Home Directory : /opt/jboss
- OpenSSO server URL : http://sso.smartlab.net:8080/opensso
- Agent URL : http://test.smartlab.net:8180/opensso-agent
- Agent Profile name : JBoss
- Agent Profile Password file name : /opt/jboss/opensso/agent.pwd
- Agent permissions gets added to java permissions policy file : false
- rename the deploy/agentapp.war file to deploy/opensso-agent.war because I used a non standard name;
- change the jboss/bin/run.sh script because the suggested procedure to add the agent classpath wasn't good for my environment; I used this script excerpt in place of the suggested one (please note that this excerpt need you to change the first line of run.sh from #!/bin/sh to #!/bin/bash.
 I then ran my JBoss test instance with /opt/jboss/bin/run.sh -c sso and everything seems working: I tested it trying to access the http://test.smartlab.net:8180/opensso-agent application being redirected to the OpenSSO login page on http://sso.smartlab.net/opensso.
I then ran my JBoss test instance with /opt/jboss/bin/run.sh -c sso and everything seems working: I tested it trying to access the http://test.smartlab.net:8180/opensso-agent application being redirected to the OpenSSO login page on http://sso.smartlab.net/opensso.The last test was about securing the JBoss JMX Console through OpenSSO. The activity required me to:
- add this snippet to the deploy/jmx-console.war/WEB-INF/web.xml file
- add this snippet to the deploy/jmx-console.war/WEB-INF/jboss-web.xml file
Ok, then let's try to log into the JBoss JMX Console, but with which credentials?!? On my first try I used the OpenSSO Administration Console superuser credentials (amAdmin/adminadmin) but I encountered a redirection loop failure thus discovering my setup wasn't ready yet. Googling a little bit I discovered this error can be simply solved adding an addition parameter for the JVM to the Tomcat configuration: JAVA_OPTS="$JAVA_OPTS -Dcom.iplanet.am.cookie.c66Encode=true".
Solved the problem and going back to the JMX Console I got a 403 (resource forbidden) error and after some investigations I discovered the easiest solution was to tell OpenSSO to simply apply a limited policy of type SSO_ONLY (Access Control > Top Level Realm > Agents > J2EE > JBoss > General add a jmx-console=SSO_ONLY map entry).
In the near future I wish to try the usage of the OpenID 2 standard on OpenSSO, I've found some instructions on another blog but I hadn't the time to investigate yet.

1 comment:
Actually the JBoss Agent 3.0 causes a redirect loop if used on top of JBossAS 5.1
Post a Comment